









Study with the several resources on Docsity

Earn points by helping other students or get them with a premium plan


Prepare for your exams
Study with the several resources on Docsity

Earn points to download
Earn points by helping other students or get them with a premium plan
Community
Ask the community for help and clear up your study doubts
Discover the best universities in your country according to Docsity users
Free resources
Download our free guides on studying techniques, anxiety management strategies, and thesis advice from Docsity tutors
The issues of web spam and propaganda in the context of the vast and omnipresent web. It discusses how anyone can be an author, the unreliability of search engines, and the techniques used by spammers and propagandists to manipulate search results and societal trust. The document also introduces the history of search engines and their evolution in dealing with spam.
Typology: Study notes
1 / 14

This page cannot be seen from the preview
Don't miss anything!









… but it can be unreliable!
Email Spam anyone?!
… you like it or not!!
Why?! How do they do it? Web Spam:
The Web is a Graph!
Access method Server and domain
Path Document
Inverted index Search engine servers Document IDs How Google (and the other search engines) Work! user query THE WEB
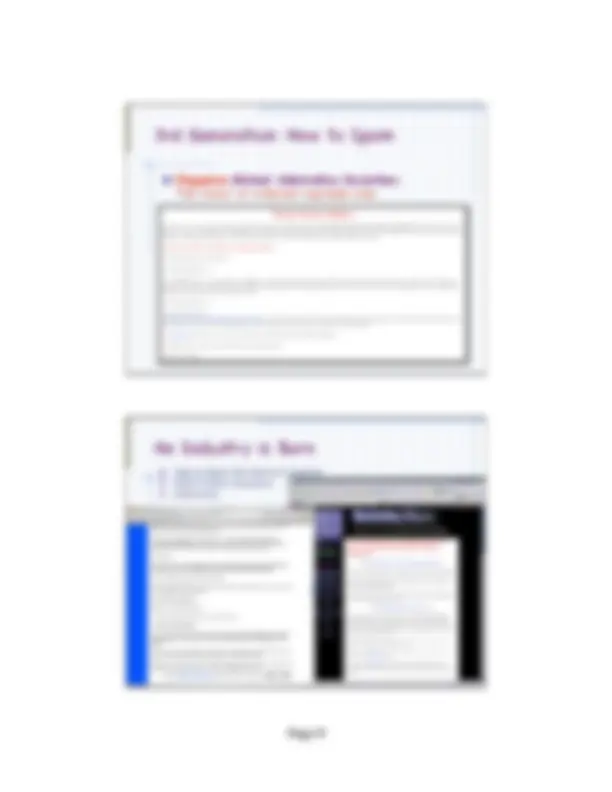
1st Generation: How to Spam! “Keyword stuffing”: Add keywords, text, to increase content similarity Searching for Jennifer Aniston? SEX SEXY MONICA LEWINSKY JENNIFER LOPEZ CLAUDIA SCHIFFER CINDY CRAWFORD JENNIFER ANNISTON GILLIAN ANDERSON MADONNA NIKI TAYLOR ELLE MACPHERSON KATE MOSS CAROL ALT TYRA BANKS FREDERIQUE KATHY IRELAND PAM ANDERSON KAREN MULDER VALERIA MAZZA SHALOM HARLOW AMBER VALLETTA LAETITA CASTA BETTIE PAGE HEIDI KLUM PATRICIA FORD DAISY FUENTES KELLY BROOK SEX SEXY MONICA LEWINSKY JENNIFER LOPEZ CLAUDIA SCHIFFER CINDY CRAWFORD JENNIFER ANNISTON GILLIAN ANDERSON MADONNA NIKI TAYLOR ELLE MACPHERSON KATE MOSS CAROL ALT TYRA BANKS FREDERIQUE KATHY IRELAND PAM ANDERSON KAREN MULDER VALERIA MAZZA SHALOM HARLOW AMBER VALLETTA LAETITA CASTA BETTIE PAGE HEIDI KLUM PATRICIA FORD DAISY FUENTES KELLY BROOK SEX SEXY MONICA LEWINSKY JENNIFER LOPEZ CLAUDIA SCHIFFER CINDY CRAWFORD JENNIFER ANNISTON GILLIAN ANDERSON MADONNA NIKI TAYLOR ELLE MACPHERSON KATE MOSS CAROL ALT TYRA BANKS FREDERIQUE KATHY IRELAND PAM ANDERSON KAREN MULDER VALERIA MAZZA SHALOM HARLOW AMBER VALLETTA LAETITA CASTA BETTIE PAGE HEIDI KLUM PATRICIA FORD DAISY FUENTES KELLY BROOK SEX SEXY MONICA LEWINSKY JENNIFER LOPEZ CLAUDIA SCHIFFER CINDY CRAWFORD JENNIFER ANNISTON GILLIAN ANDERSON MADONNA NIKI TAYLOR ELLE MACPHERSON KATE MOSS CAROL ALT TYRA BANKS FREDERIQUE KATHY IRELAND PAM ANDERSON KAREN MULDER VALERIA MAZZA SHALOM HARLOW AMBER VALLETTA LAETITA CASTA BETTIE PAGE HEIDI KLUM PATRICIA FORD DAISY FUENTES KELLY BROOK 2nd Generation: Add Popularity! A hyperlink from a page in site A to some page in site B is considered a popularity vote from site A to site B Rank similar documents according to popularity How To Spam?
2nd Generation: How to Spam! Create “Link Farms”: Heavily interconnected sites spam popularity 3rd Generation: Add Reputation! The reputation “PageRank” of a page Pi = the sum of a fraction of the reputations of all pages Pj that point to Pi Idea similar to academic co-citations Beautiful Math behind it
How To Spam?
Unanswered Spam Attacks!
Search Engines vs Web Spam!
Is there a pattern on how to spam? Can you guess what they will do?
And Now For Something Completely(?) Different!
Societal Trust is (also) a Graph! Weighted Directed Graph of Nodes and Weighted Arcs
Then what is Propaganda?
How to modify the Trust Graph?
Cognitive Hacking and Cyber Trust!
How (not) To Solve The Problem!
Living in Cyberspace! Critical Thinking, Education
Cyber-social Structures that mimic Societal ones
A Search Engine per Browser
Thank You!! PMetaxas@wellesley.edu