




Study with the several resources on Docsity

Earn points by helping other students or get them with a premium plan


Prepare for your exams
Study with the several resources on Docsity

Earn points to download
Earn points by helping other students or get them with a premium plan
Community
Ask the community for help and clear up your study doubts
Discover the best universities in your country according to Docsity users
Free resources
Download our free guides on studying techniques, anxiety management strategies, and thesis advice from Docsity tutors
Material Type: Lab; Class: Computer Network Security; Subject: Electrcl & Computer Engr; University: University of the Pacific; Term: Fall 2007;
Typology: Lab Reports
1 / 11

This page cannot be seen from the preview
Don't miss anything!







LAB 12
If any of your force be killed orcaptured, the secretary willdisavow any knowledge of youractions...this tape will self destructin 5 seconds... Good Luck, Jim
-site
site
scripting (XSS)scripting (XSS)
Scenario
You have a remote target, a popular forum website that yourhuman targets use to post comments to one another. Yourtask is to use XSS to modify that site in a way that tricksyour targets into giving you information. Barring that, atleast let the site owner there’s a problem by inserting an alert popup.
12/20/
LAB 12
popup. Choose your target:
http://www.jkandtc.com/blog
everyone shares,
fighting each other!
or http://www.jkandtc.com/
n
/blog
yours to do whatever!
Where
n
Potential Show Stoppers
LAB 12
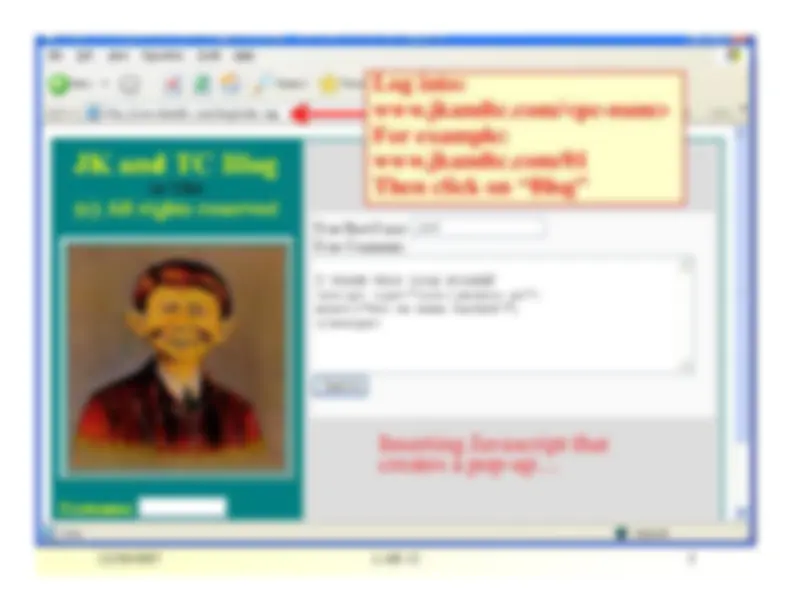
Log into:www.jkandtc.com/<pc-num>For example:www.jkandtc.com/01Then click on “Blog” LAB 12
Inserting Javascript thatcreates a pop-up…
LAB 12
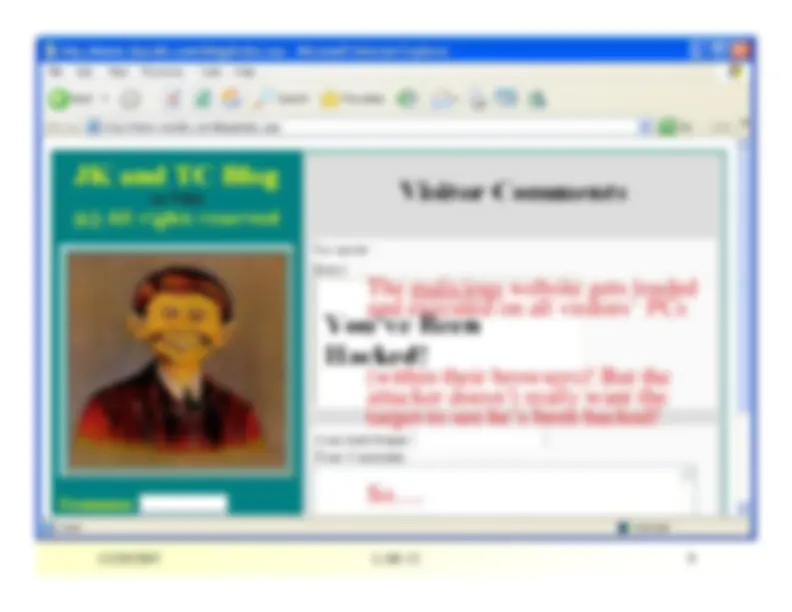
What appears after the pop-up is closed
Attacker’s “comment”
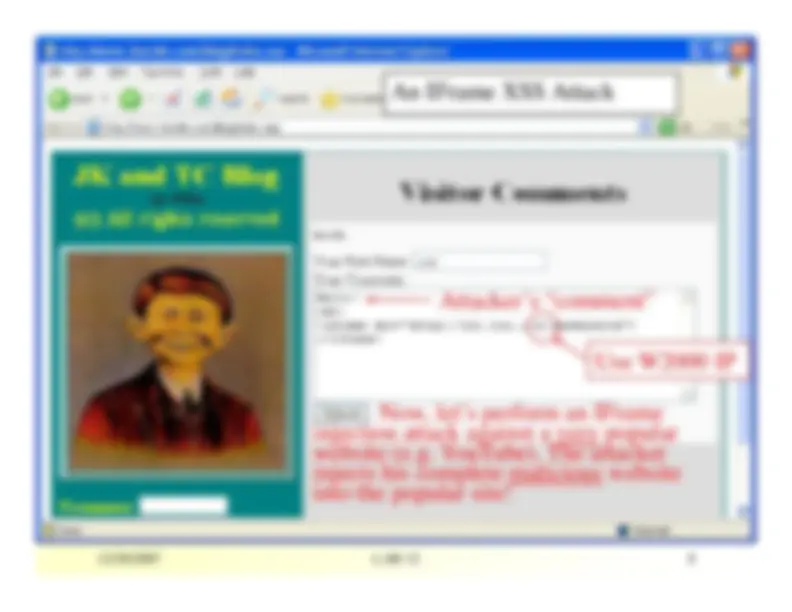
An IFrame XSS Attack
LAB 12
Now, let’s perform an IFrame
injection attack against a very
popular
website (e.g. YouTube). The attackerinjects his complete malicious
website
into the popular site!
Attacker’s “comment”
Use W2000 IP
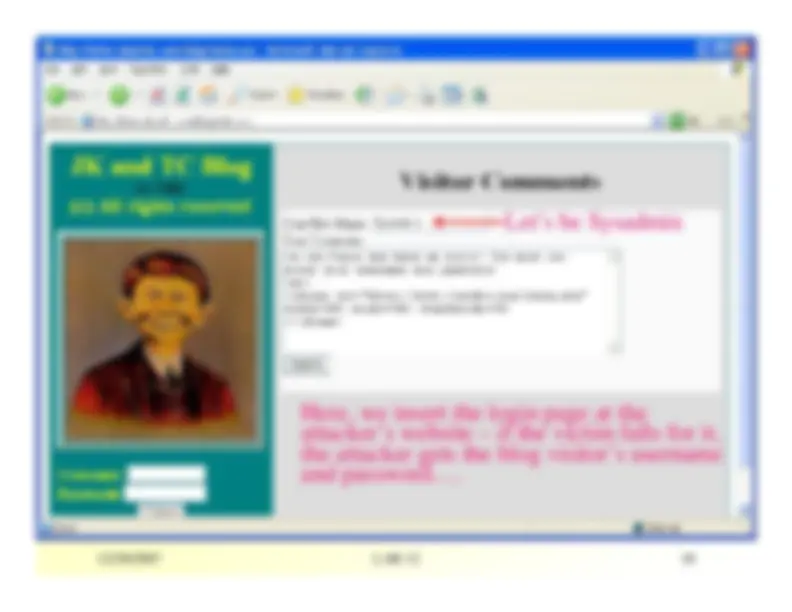
Let’s be Sysadmin
LAB 12
Here, we insert the login page at theattacker’s website – if the victim falls for it,the attacker gets the blog visitor’s usernameand password….