









Study with the several resources on Docsity

Earn points by helping other students or get them with a premium plan


Prepare for your exams
Study with the several resources on Docsity

Earn points to download
Earn points by helping other students or get them with a premium plan
Community
Ask the community for help and clear up your study doubts
Discover the best universities in your country according to Docsity users
Free resources
Download our free guides on studying techniques, anxiety management strategies, and thesis advice from Docsity tutors
Material Type: Notes; Class: Information Technology and Society; Subject: Interdisciplinary Studies; University: Southern Illinois University Edwardsville; Term: Unknown 1989;
Typology: Study notes
1 / 17

This page cannot be seen from the preview
Don't miss anything!










Dr. Stephen Blythe Department of Computer Science SIUE
Three key “aspects” everyone wants:
freedom from intrusion
control of personal information freedom from surveillance
A database (DB) is:
collection of “related” data
that is easy to access quickly
Examples:
credit bureaus (Experian, Equifax, ...)
restaurant reviews
airline reservations (scheduled and completed) survey results
Use of data in a manner not originally intended
Came about as storage become cheaper and larger
complete works of Shakespeare: ~5 Megabytes(MB)
DVD: ~17 Gigabytes (GB)
modern desktop hard drive: ~200 GB
Costs:
100 MB circa 1990: ~$400 (very few utilized) 200 GB today: ~$100 (most PC’s have)
Cell Phones & Pagers
can be used to locate 911 calls (“tracking”)
Global Positioning Systems (GPS)
automatically guide military jets onto carriers
Microscopic Cameras embedded in cell phones
Inaccurate information can get in databases
false (usually negative) credit reports
denial of boarding on aircraft
Secondary use by criminals (ex. pedophiles) Secondary use by government
Satellite Imaging
http://maps.google.com
http://gis.stlouisco.com
these are relatively “lighweight” examples!
Full Body Security X-Rays Closed Circuit Television (CCTV)
One approach is to “let the market fix it”
relies on companies to address issues
a.k.a. “self regulation”
Examples:
mailing list companies renting (not selling)
forcing payment to get survey results re-imbursing for survey participation
Watch out for passwords ....
sites may store your password these sites might be hacked
Watch out for passwords ....
sites may store your password
these sites might be hacked
stay away from sites that can send you your original password. Why?
they have stored your password in plain text better option is to store a “checksum” password
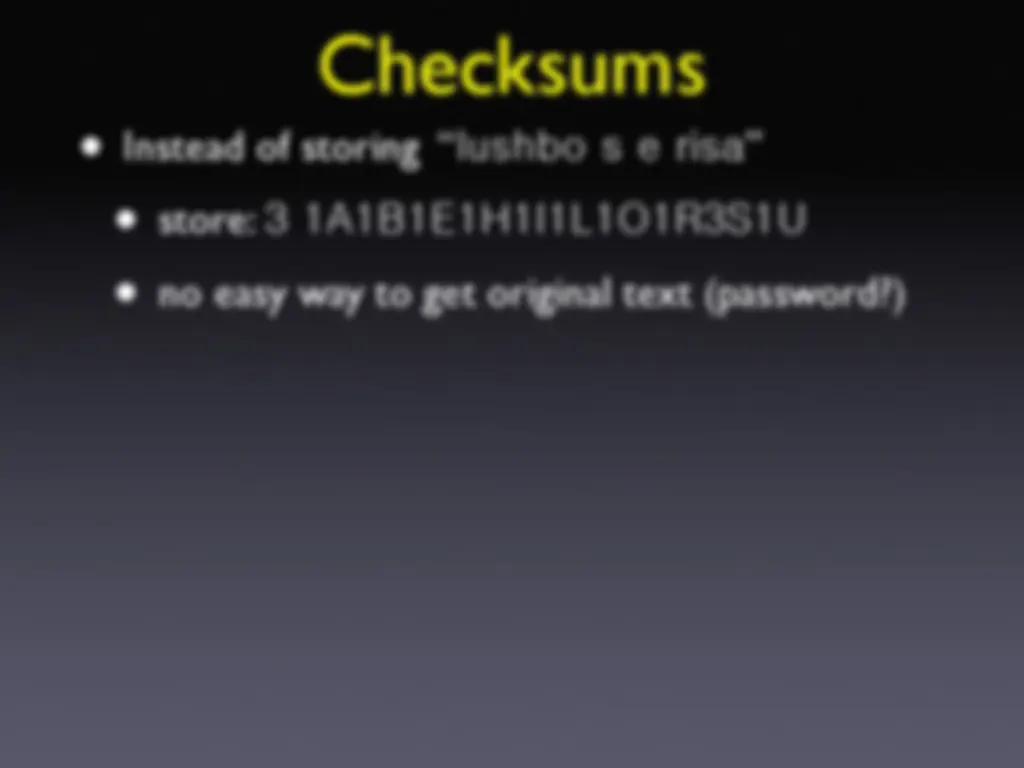
Instead of storing “ ”
store:
no easy way to get original text (password?)
not the greatest checksum in the world ...
gives the same thing
this is known as a “collision”
MD5 checksums (hashes) generate 1024 bits
no immediate “character counts” contained very hard to make a “collision” match
store checksum instead of password
now, if password database is hacked ...
all the hacker gets is garbage checksum strings
no easy way to get original text (password)
can certify/verify software this way
manufacturer creates hash of binary software
posts resulting hash (often MD5) to Internet
purchaser then hashes purchased software if hashes match, software is certified/verified