




Study with the several resources on Docsity

Earn points by helping other students or get them with a premium plan


Prepare for your exams
Study with the several resources on Docsity

Earn points to download
Earn points by helping other students or get them with a premium plan
Community
Ask the community for help and clear up your study doubts
Discover the best universities in your country according to Docsity users
Free resources
Download our free guides on studying techniques, anxiety management strategies, and thesis advice from Docsity tutors
A series of multiple-choice questions and answers related to Apex One, a security software solution. The questions cover topics such as Trusted Program List, Lockdown Mode, Security Agent components, Endpoint Sensor, and File Census. explanations for each answer and is intended to serve as a study guide for individuals preparing for an Apex One exam.
Typology: Exams
1 / 20

This page cannot be seen from the preview
Don't miss anything!













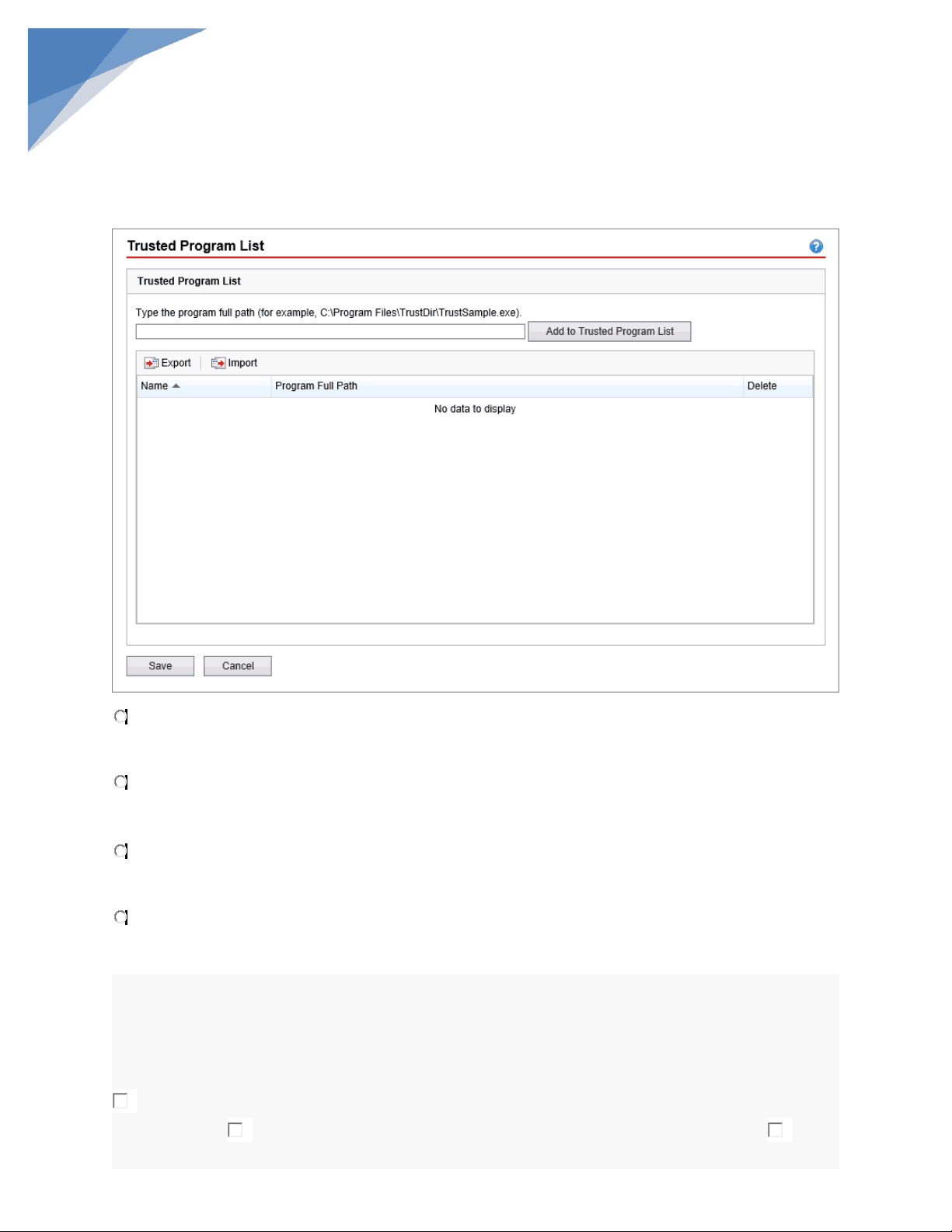
Which of the following statements is FALSE regarding the use of the Trusted Program List as displayed in the exhibit? Security Agents skip scanning of programs or processes in the Trusted Program List during real- time and behavior monitoring scans. You can add files to the Trusted Program List if they are not located in the Windows system directory and have a valid digital signature. Security Agents skip scanning of programs or processes in the Trusted Program List during real- time, manual, scheduled and scan now scans. Scan performance on endpoints can be improved by using the Trusted Program List since processes are excluded from suspicious activity monitoring. When in Lockdown Mode, Apex One blocks all applications not identified during an inventory scan. Applications from trusted vendors can be excluded from Lockdown. When in Lockdown Mode, the endpoint does not permit access to any application that do not Multiple Choice
Which of the following statements are TRUE regarding Lockdown Mode in Apex One Application Control policies? Select all answers that apply.
Single choice
During the installation of the Apex One Server, the Setup Wizard displays a port that will be used for Apex One Server-Agent communication, as displayed in the exhibit. How is this port assigned? The Setup Wizard does not assign the port; you must type a port number manually. The Setup Wizard scans ports on the Apex One Server and selects a port that is not being used. Port 21112 is assigned automatically, but the port can be changed, if required, during the Setup Wizard. The port assignment is read from an Apex Central configuration file. Single choice specifically match Allow criteria. When in Lockdown Mode, assessment mode is automatically disabled.
Specifying one or more gateway or reference server addresses allows the Web Reputation Service to block known browser exploits. Specifying one or more gateway or reference server addresses creates automatic exceptions in the firewall configuration. Specifying one or more gateway or reference servers addresses allows Security Agents to determine whether they are on an internal or an external network. Specifying one or more gateway or reference server addresses allows the Web Reputation Services Proxy to access the Internet. Single choice
Which of the following activities will NOT be captured as attacks by Behavior Monitoring in Apex One? A Malicious program adds or modifies autostart entries in the Windows Registry. This will automatically launch the malicious program when the computer starts. A malicious program is downloaded from the Web through Internet Explorer or Outlook. A malicious application attempts to replace a system file with another file of the same name. A malicious program modifies Windows shell settings to associate themselves to certain file types, allowing the malicious program to launch automatically when an end-user attempts to open the associated file in Windows Explorer. Running the Security Agent Uninstall Program. Using the Agent Mover Tool (IpXfer.exe) to move the Agent to another endpoint computer. Uninstalling the Security Agent through the Apex One Web Management console. Manually uninstalling the services, files and registry information. Single choice
Which of the following is NOT a valid method for removing the Security Agent from an endpoint computer? Multiple Choice
Multiple Choice
What are some of the limitations of a Security Agent running in Independent Mode? Select all answers that apply. The Security Agent denies access to shared folders. The Security Agent does not run real- time scans. The Security Agent does not accept policy settings from the Apex One Server. The Security Agent does not initiate scan commands from the Apex One Server. Single choice
Which of the following statements regarding the Newly Encountered Programs feature of Behavior Monitoring is FALSE? Applications can be added to a white list to bypass the New Encountered Programs feature. This will allow programs to execute regardless of their prevalence and maturity. End users can be prompted to allow programs with low prevalence or maturity. Assessment Mode provides a trial period for evaluating Apex One protection before requiring valid activation codes to be provided. Assessment Mode allows administrator to maintain visibility of roaming users even when they are not using a VPN connection into the corporate network. Assessment Mode provides a time period where files evaluated by the Security Agent are submitted to the Predictive Machine Learning model. Submissions provided while in Assessment Mode train the model to identify potential malware for your installation of Apex One. Assessment Mode allows an administrator to evaluate items that Apex One detects as spyware/grayware or to monitor Web site access. When Assessment Mode is enabled, detections are logged only. Single choice
Which of the following best describes Assessment Mode in Apex One? Files in the Security Agent folder on the endpoint computer Smart Scan Agent Patterns, and Conventional Patterns Security Agent Registry settings Security Agent services Which of the following Security Agent components are protected from unauthorized modifications using the Agent Self-protection features in Apex One? Select all answers that apply.
The Agent Tree Scope must be configured. The Trace Route Scope must be configured. The Active Directory/IP Scope must be configured. The Port Range Scope must be configured. Single choice
Which of the following must be configured before taking advantage of the Unmanaged Endpoints feature in Apex One? Single choice
Which one of the following is NOT a capability of the Apex One Ransomware protection? Blocks processes commonly associated with ransomware. Decrypts ransomware encrypted files. Automatically backs up and restores files encrypted by unauthorized operations. Protects documents against unauthorized encryption operations. Single choice
What is the role of the Reference Server configuration as displayed in the exhibit? Security Agents will always have the appropriate settings for their domain, there is no need to verify this. The administrator can run a Compliance Report and verify the results on the Settings tab. Any endpoints in the domain with inconsistent settings will be displayed. The administrator can verify the settings from the Agent Details.
Security Agents used this configuration to identify alternate update sources. If an Agent is unable to contact the Primary Update Source, it will attempt to connect to the Reference Server. Security Agents used this configuration to identify secondary Apex One Servers. When a Security Agent is moved from one Server to another, the servers listed as Reference Servers will be available as destination choices in the Move Agent window. Security Agents use this configuration to determine which policy or profile to use. If a Security Agent cannot connect to the server listed in this configuration, the Agent status changes to offline and the policy or profile for external agents is used. Security Agents use this configuration to determine whether they should connect directly to the Apex One Server or to the Edge Relay Server. In the Reference Server window, provide the details of the Edge Relay Server and port number. Multiple Choice
Target endpoints receiving policy settings through Apex Central can be identified using Filter by Criteria or Specify Agent(s) as displayed in the exhibit. Which of the following statement are TRUE regarding these two options? Select all the answers that apply.
If no rules are matched during the grouping operation, the administrator will be prompted to select a group in the Apex One Agent tree. If no rules are matched during the grouping operation, the Agents are placed in a group called Default. If no rules are matched during the grouping operation, the Agents will not be displayed in the Apex One Agent tree. If no rules are matched during the grouping operation, the Agents are placed in the first group in the list. Single choice
Multiple automatic grouping rules are created to sort Security Agents in the Apex One Agent tree. How will Apex One handle Security Agents that do not match any of the grouping rules? Single choice
When Smart Feedback is enabled on an Apex One Server, where does the Security Agent send the information? It is sent to the Smart Protection Network. It is sent to the Site Safety Center. It is sent to the Smart Feedback Server. It is sent to a Smart Protection Server. Multiple Choice
A new IP Address Grouping is configured as in the exhibit. The new grouping called Lab is created, but when checking the Agent List, no Agents are displayed in the group even though Endpoint Sensor provides the ability to investigate both the historical and current state of a Policies using Endpoint Sensor are deployed from Apex Central. managed endpoint. A separate Endpoint Sensor Agent must be installed on the endpoint computer. Endpoint Sensor records metadata related to activities occurring on the endpoint computer. This data is forwarded to Apex One on a regular basis for storage in the database. Which of the following statements are TRUE regarding the use of Endpoint Sensor with Apex One? Select all answers that apply.
Agents do exist within the IP address range. Which of the following events will trigger the addition of the Agents to the group? Select all answers that apply. Agents are added to the group when their connection status changes from offline to online. Agents are added to the group when the administrator runs the Sort Client operation.
Custom Security Agent grouping rules are configured. An endpoint computer hosting a Security Agent that does not match any of these grouping rules is created. Where will this computer appear in the Security Agent tree? This endpoint computer will not appear in the Security Agent tree until it matches one of the grouping rules. This endpoint computer will appear under a domain called "Default" in the Security Agent Tree. This endpoint computer will appear under the domain that has the least number of Security Agents registered in the Security Agent tree. This endpoint computer will appear under a domain called "No Domain" in the Security Agent tree. Multiple Choice
The Apex One Security Agent icon in the Windows System Tray displays with the icon displayed in the exhibit. Which of the following answers describes the state of the Agent? Select all the answers that apply. The Security Agent does not have access to a Smart Protection source. The Security Agent does not have a connection to the Apex One Server. The Real-time Scan service on the Security Agent is not running. The Security Agent has a connection to the Apex One Server. Multiple Choice Fileblocked.log Cache.dat OfcUrlf.log Blockedurl.log Single choice
Web Reputation is configured to block a specific URL. In which log file is a corresponding entry added when a user attempts to access the blocked URL?
Single choice
How can you locate endpoints on the network that do not have a Security Agent installed? Use Advanced Search in the Apex One Web Management console and select the Unprotected parameter. Click Assessment > Unmanaged Endpoints in the Apex One Web Management console and click Define Scope to select a branch in the Active Directory tree or an IP address range. Click Agents > Unmanaged Agents in the Web Management console and use the Search feature to locate the unprotected Agents. Click Agents > Agent Management in the Web Management console and search through the list for any Agents displaying the Unprotected icon. Single choice
Apex One can query Active Directory to identify endpoint using third-party security software and target them for uninstallation. Active Directory can be used to automatically group agents based on an Active Directory domain and map them to domains in the Apex One Security Agent tree. Apex One can query Active Directory to locate endpoints computers without Security Agents installed. Administrative capabilities in the Apex One Web Management console can be assigned to Active Directory accounts.
Which of the following Apex One features are enabled by integrating with Microsoft Active Directory? Select all the answers that apply. The Predictive Machine Learning model is fed a large number of good and bad files to teach it to identify malware. The Security Agent extracts features of the file and submits it to the Predictive Machine Learning model to make a decision. Predictive Machine Learning in Apex One works on files and processes. Predictive Machine Learning uses patterns contained in locally stored files to make a decision. Single choice
Which of the following statements regarding Predictive Machine Learning is FALSE?
Multiple Choice
Predictive Machine Learning in Apex One can examine files from which of the following channels? Select all answers that apply. USB Selected Web browsers Microsoft Outlook Files copied from a network share using Windows Explorer The Windows Firewall must be temporarily disabled during the installation of the Security Agent. The endpoint computer must be running the Windows Remote Registry service. Remote installation of Agents can only be performed on Server platforms. The endpoint computer must be registered in Active Directory. When this setting is enabled, Security Agents are able to access the Internet through a Web proxy. Single choice
Which of the following statements describes a valid use for the Smart Protection Service Proxy setting displayed in the exhibit?
Single choice
Which of the following statements regarding the Apex One Firewall is TRUE? The Apex One Firewall can be enabled/disabled on Agents at any level in the Agent Tree. The Apex One Firewall can only be enabled/disabled on Agents at the global level in the Agent tree. The Apex One Firewall can only be enabled/disabled on Agents at the Security Agent level in the Agent tree. The Apex One Firewall can only be enabled/disabled on Agents at the domain level in the Agent tree. Single choice
When this setting is enabled, Machine Learning requests are proxied through the Smart Protection Server. This allows endpoint computers with unreliable Internet connections to enable Predictive Machine Learning checks. When this setting is enabled, Smart Scan becomes available in addition to conventional scanning. This allows endpoint computers to access a cloud-based repository of malware information on the Smart Protection Network. When this setting is enabled, Machine Learning requests by remote Security Agents are proxied to the Smart Protection Server through the Edge Relay Server. This allows endpoint computers outside of the network to enable Predictive Machine Learning checks. Click "Enable Apex One Edge Relay Server" during the Apex One Setup Wizard. Run the Edge Relay Server setup application on the Apex One Server and specify the IP address of the target server when prompted. Click "Enable Apex One Edge Relay Server" under the Administration Settings in the Apex One Web Management console. On the target server, run the Edge Relay Server setup application obtained from the Apex One Server. Single choice
Which of the following correctly describes the method of deploying an Apex One Edge Relay Server?
Single choice
Which of the following Security Agent deployment methods allows you to select the Scan Mode for the Agent as part of the setup? Logon script Remote install Web install Security Agent Packager Single choice
Which of the following items is NOT required to enable Browser Exploit Protection? Web Reputation Apex One Data Protection The Apex One Edge Relay Server Apex One (Mac) An Integrated Smart Protection Server Single choice
Which of the following Apex One Server components can you install as part of the setup process?
Certified Safe Software List File hash File reputation Keywords Multiple Choice
Which of the following are valid criteria that can be used to define applications to be blocked through Application Control in Apex One? Select all the answers that apply. Advanced Protection Service Behavior Monitoring Relevant browser plug-in installed Single choice
Which of the following statements regarding File Census in Apex One is FALSE? File Census checks for prevalence of a file. File Census can check on HTTP but not HTTPS channels. File Census is a service provided through the Smart Protection Network. File Census checks for maturity of a file. In the Apex One Web Management console, click Agents > Agent Management and select the Agent to be moved. Click Manage Agent Tree > Move Agent. Run the Server Tuner tool and identify the name of the Agent to be moved and the details of the new Apex One Server. Open the Security Agent console and specify the new Apex One Server location. Run the Apex One Update Agent utility and identify the details of the new Apex One Server. Single choice
Which of the following is a valid method for moving a registered Security Agent to a different Apex One Server?